PortSec
Maritime transport is of central importance for the German economy. In order to ensure the smooth flow of cargo and accompanying data through the seaports, electronic data transmission systems for ports (port telematics systems) or Port Community Systems (PCS) are used. They can be seen as centralized data hubs, connecting companies and authorities involved in maritime transport, such as shipowners, freight forwarders, terminals, railways and Customs. As part of the Critical Infrastructure in traffic and transport, failures or disturbances of respective systems can lead to massive problems in port operation, in extreme cases even to a standstill. IT attacks on port telematics systems can – depending on the duration – even lead to bottlenecks in the supply of industries and population.
Manipulation of data, for example in case of containers loaded with dangerous goods, could lead to storage without obtaining the legally required separation instructions. This may result in chemical reactions of hazardous substances and eventually lead to fire or explosion. Confidential data could be tapped using manipulated user accounts in order to prepare for criminal acts like cargo theft or smuggling of drugs.
The objective of the PortSec project is to develop a systematic and comprehensive IT risk management in port telematics, taking into account the underlying software architecture and including legal and economic security requirements. The software-based approach focuses on the prevention of attacks rather than their detection and defence. This approach is particularly innovative and has not yet been applied in existing procedural models and standards for the establishment of information security management systems (ISMS).
THREAT ANALYSIS
With regard to the analysis of potential threats, scenarios will be developed describing possible IT attacks on port telematics systems. For this purpose, the domain-specific business processes in the area of port communication will be analyzed. The security requirements of the processes and the processed data will be assessed as well. The analysis is designed to identify possible weaknesses, primarily related to interfaces used for communication via the Internet. In addition, the systems are examined regarding protection factors like availability, confidentiality, and integrity.
Based on the results of the threat analysis, relevant attack scenarios will be defined, and associated economic and business risks will be evaluated with regard to potential damage. For this purpose, each individual scenario will be assessed with regard to the probability of occurrence, vulnerability and consequences in order to evaluate the effects and resulting damage of possible attacks on the port telematics system operator, the port industry, and downstream logistics processes. The impact of attacks and resulting effects on the economy will be examined as well. Previous similar attacks will be analyzed in order to complete the picture of the threat scenarios.
A further objective of the project is the development of a method by which domain knowledge can be transferred in a formal way into the knowledge database to be developed. A respective concept will be developed followed by the implementation of a procedure which facilitates the input of domain knowledge in an automated and formalized manner. Finally, the domain knowledge about the dangers and the resulting risks will be transferred to the knowledge database. In that way, the knowledge can later be used for testing procedures.
AUTOMATED TESTING OF SOFTWARE
First, the implemented software architecture is automatically extracted from the source code of the port telematics system, employing static and dynamic program analyses (1). This step is necessary, since PCS consist of legacy software, which often lacks exact and up-to-date architectural descriptions. The software architecture analysis enables the identification of fundamental security risks of the software with regard to possible cyber attacks. The redesigned software architecture is then supplemented by descriptions of the network in which the PCS is operated (2). The network infrastructure is thereby detected automatically. Here, we can refer to preparatory work in which information about the IT infrastructure (assets) is managed with the aid of ontologies.
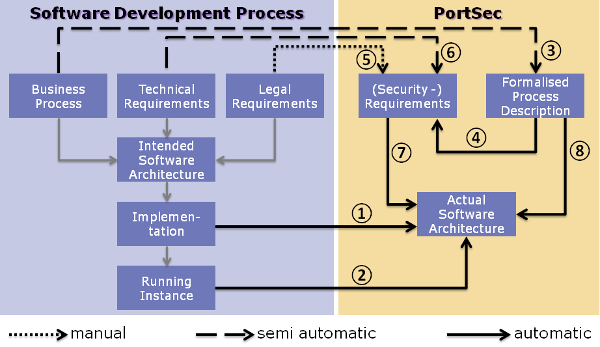
To consider specific security requirements for port telematics systems, the business processes and corresponding legal and business requirements are formally represented (3). As a result, a security evaluator can uncover situations in which unauthorized access to restricted business processes is possible and organizational control rules are circumvented (such as the task separation or the four-eye principle). This step ensures that the security requirements are in accordance with the legal and organizational requirements applicable to the operation and utilization of port telematics systems. The security requirements to be tested are derived from the formal descriptions of business processes (4), legal / economic requirements (5) as well as technical requirements (6).
In the next step, the actually implemented system and software architecture is tested with respect to the security requirements and the actual business process descriptions. This step leads to the identification of specific risks for port telematics (e.g., is it possible that an employee without authorization changes the declaration of dangerous goods containers due to excessive access rights?). At the same time, more general technical security risks are identified, e.g. insecure use of software frameworks (like JEE, Struts, Spring) or incorrect encryption.
INDUSTRY-SPECIFIC SECURITY STANDARD
The German law for the security enhancement of information technology systems (IT security law) (German), in force since July 2015, represents the consistent development of the German Federal Government's efforts to enable IT systems and digital infrastructures in Germany to be the safest and most secure in the world. Especially in the area of critical infrastructures (KRITIS), a failure or impairment of the provision of services could result in dramatic consequences for the economy, the state, and the society in Germany. The availability and security of IT systems plays an important and central role, especially in the field of critical infrastructures.
The IT security law allows operators of critical infrastructures and their associated industries to define branch-specific security standards together with the German Federal Office for Information Security (BSI). Building on the results of the PortSec research project, a sector-specific security standard for port telematics systems (maritime transport and traffic) is developed supporting the IT security law and ensuring compatibility with comparable and supplementary standards. The development of normative controls, which - similar to Annex A of ISO / IEC 27019 - must be considered as an addition to an existing ISO / IEC 27001 certification - is planned. The security standard to be developed is discussed and coordinated with relevant stakeholders in the field and the German Federal Office for Information Security (BSI) as the responsible agency in accordance with the IT Security Act. Furthermore, relevant industry associations will be involved in the activities.
The industry-specific security standard to be developed consists, on the one hand, of an audit scheme which defines the scope, depth and methods of testing. On the other hand, the security standard includes a certification scheme which specifies the processes for a multi-stage certification process and defines the life cycle of certificates, auditors and test bodies. This is particularly important as the IT Security Act requires all critical infrastructure operators to provide a proof of compliance with all requirements, explicitly calling for security audits and certifications.
Within the framework of PortSec, an audit and certification concept will be developed, considering PortSec results, which can be used by all operators of critical infrastructures in the area of maritime transport and traffic.
EVALUATION AND TRANSFER
In order to evaluate the usability and acceptance of the developed software demonstrators, appropriate test cases will be prepared and validated. Studies on usability are conducted together with end users in order to evaluate the acceptance of the software solutions. This includes controlled experiments, expert interviews, and think-aloud tests with developers, software architects, and security experts.
The methods and software demonstrators developed in the PortSec project are focusing at IT risk management in the harbour area. The PortSec approach is finally evaluated for transferability to other technologies (e.g., programming languages) and industries (e.g., general logistics) and how the PortSec results can be transferred technically or with regard to the domain.


Funding notice



